AI-Powered Cybersecurity Solutions
Advanced threat detection and automated security operations for the modern SOC
Intelligent Security Agents for the Modern SOC
HARES Cybersecurity Solutions introduces a groundbreaking approach to Security Operations Centers (SOCs) by deploying AI-driven agents that handle complex threat detection, investigation, and response in real-time.
Reduce analyst burnout through intelligent automation
Detect threats earlier with AI-driven behavioral analysis
Improve response times with automated workflows
Trusted by Leading Organizations
Operational in critical security infrastructures
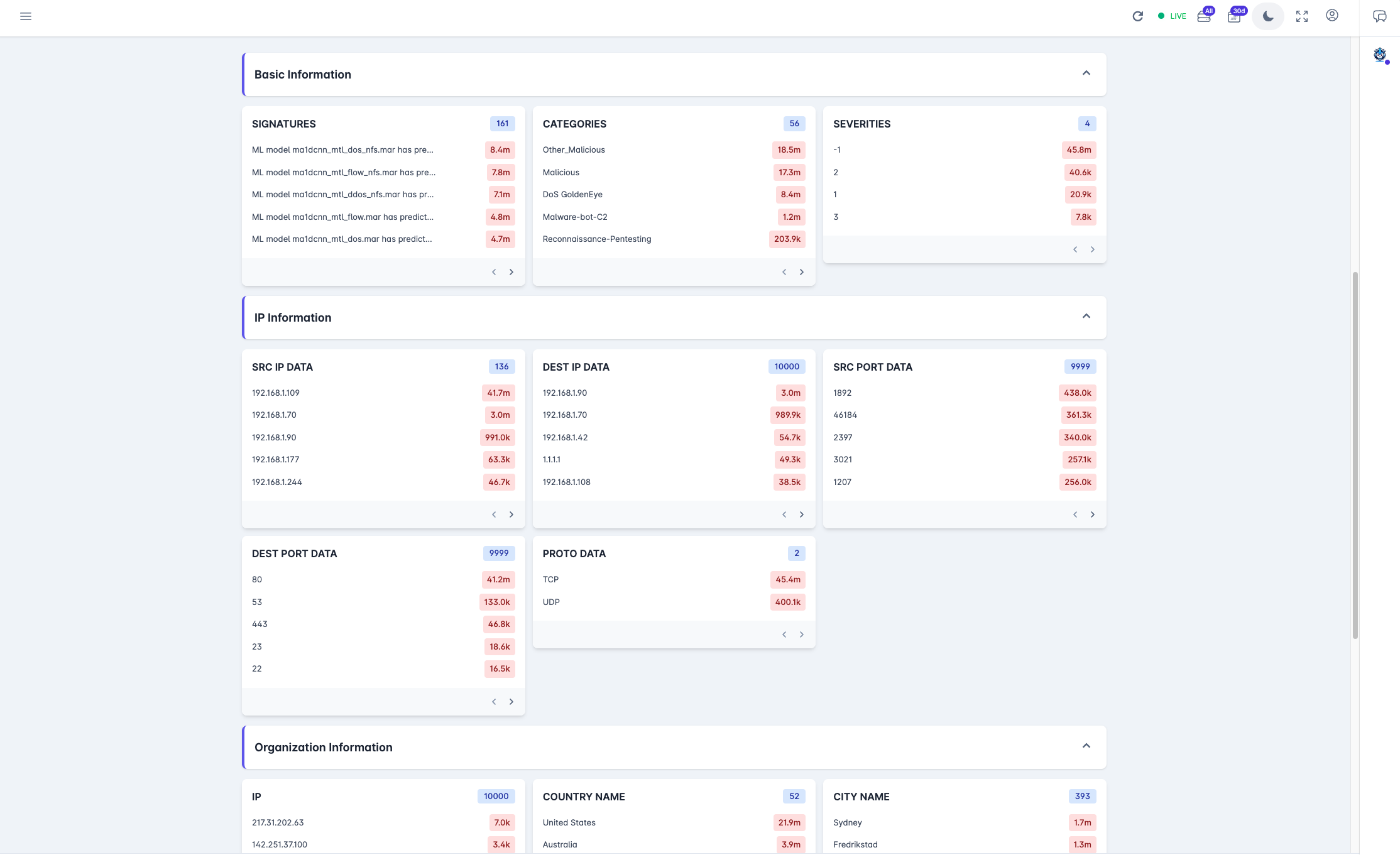
HARES NET
A sophisticated hybrid intrusion detection system with AI-driven anomaly detection and advanced network visibility.
Enhanced Visibility
Real-time monitoring of network telemetry and endpoint data for complete visibility.
AI-Driven Analysis
Machine learning models identify patterns and anomalies human analysts might miss.
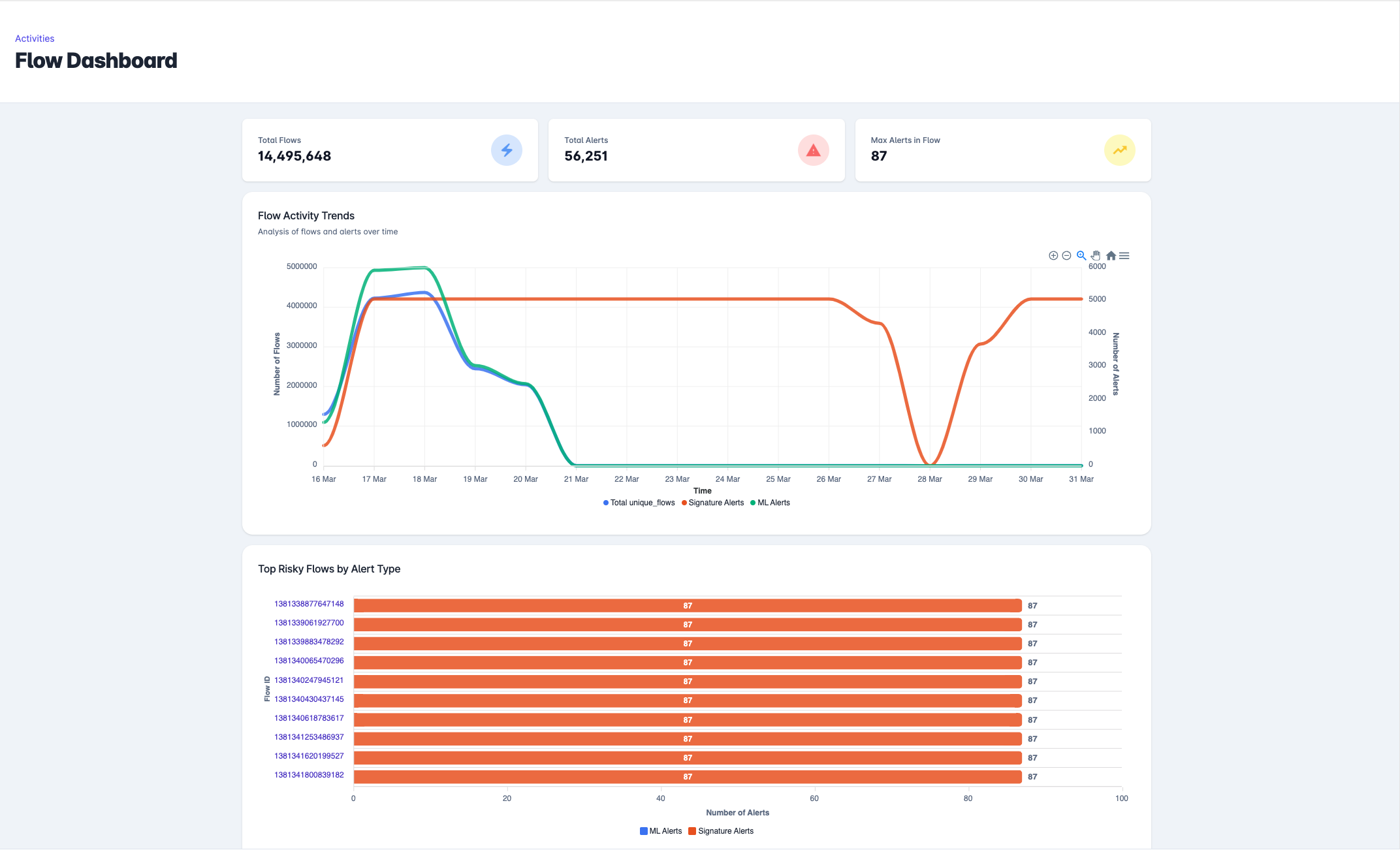
HARES Hunter
An intelligent threat-hunting assistant that proactively identifies threats using AI-driven hypotheses and contextual analysis.
Proactive Detection
Identifies potential threats before they manifest as major incidents.
Collaborative Intelligence
Works alongside analysts to explore potential compromise paths.
HARES VIBER SOC
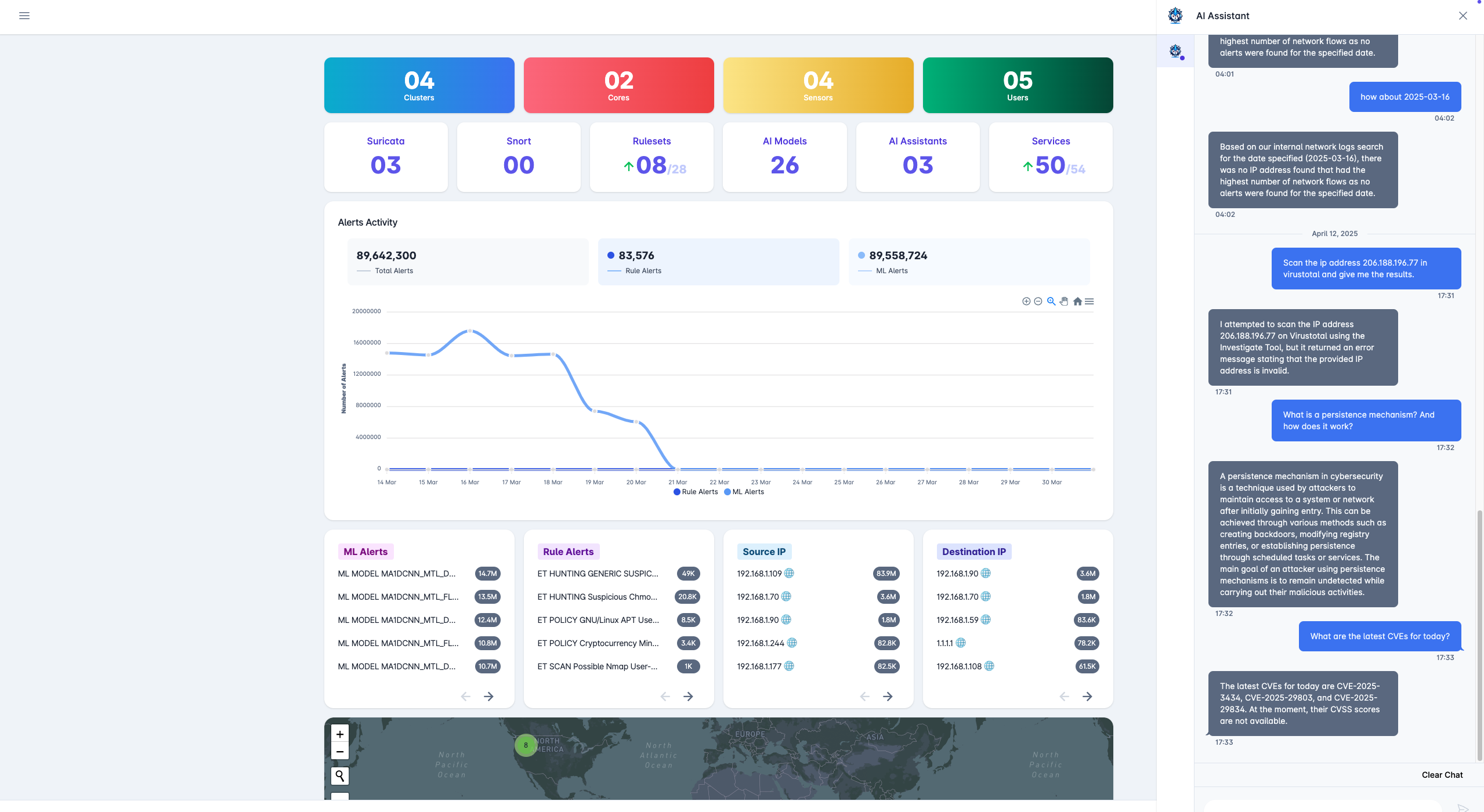
Our flagship SOC assistant acts as a digital analyst, automating alert triage, ticket generation, and providing a conversational interface for security operations.
Automated Workflows
Streamlines alert triage, ticket generation, and report writing.
Conversational Interface
Natural language queries for threat analysis and incident management.
Sovereign Network Intrusion Detection System
Advanced network security with full data sovereignty

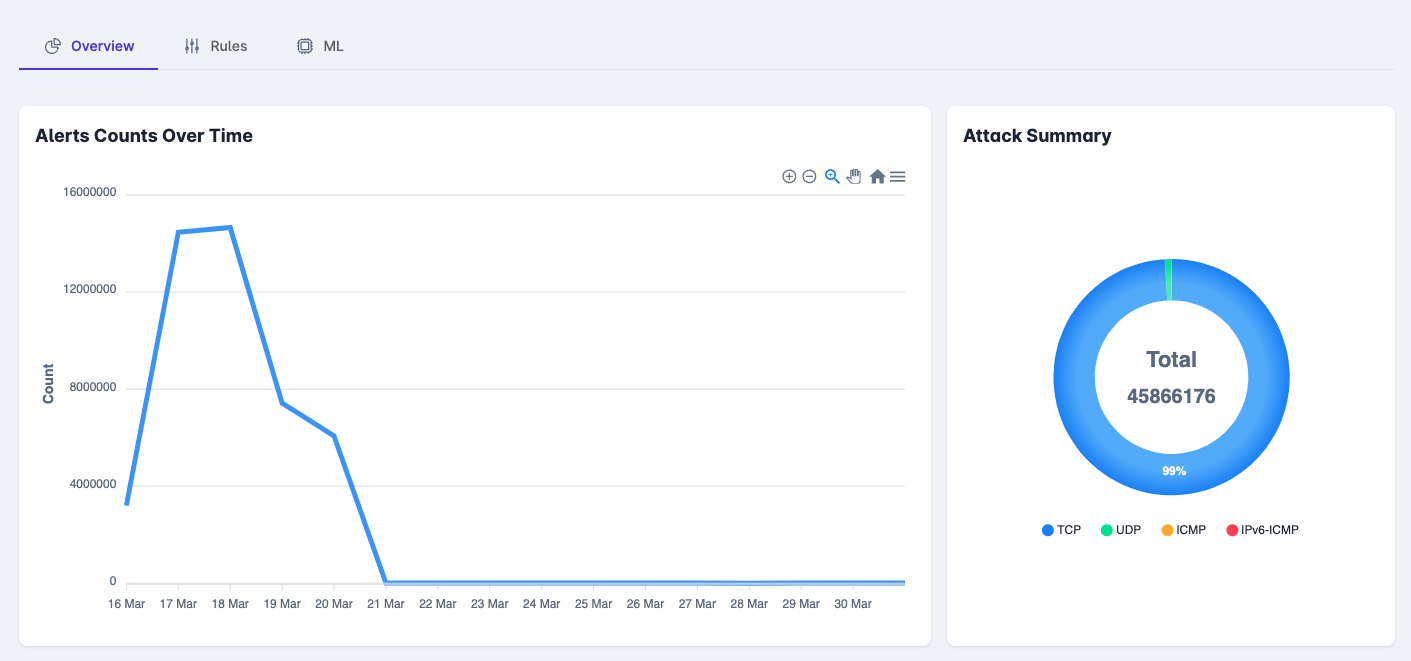

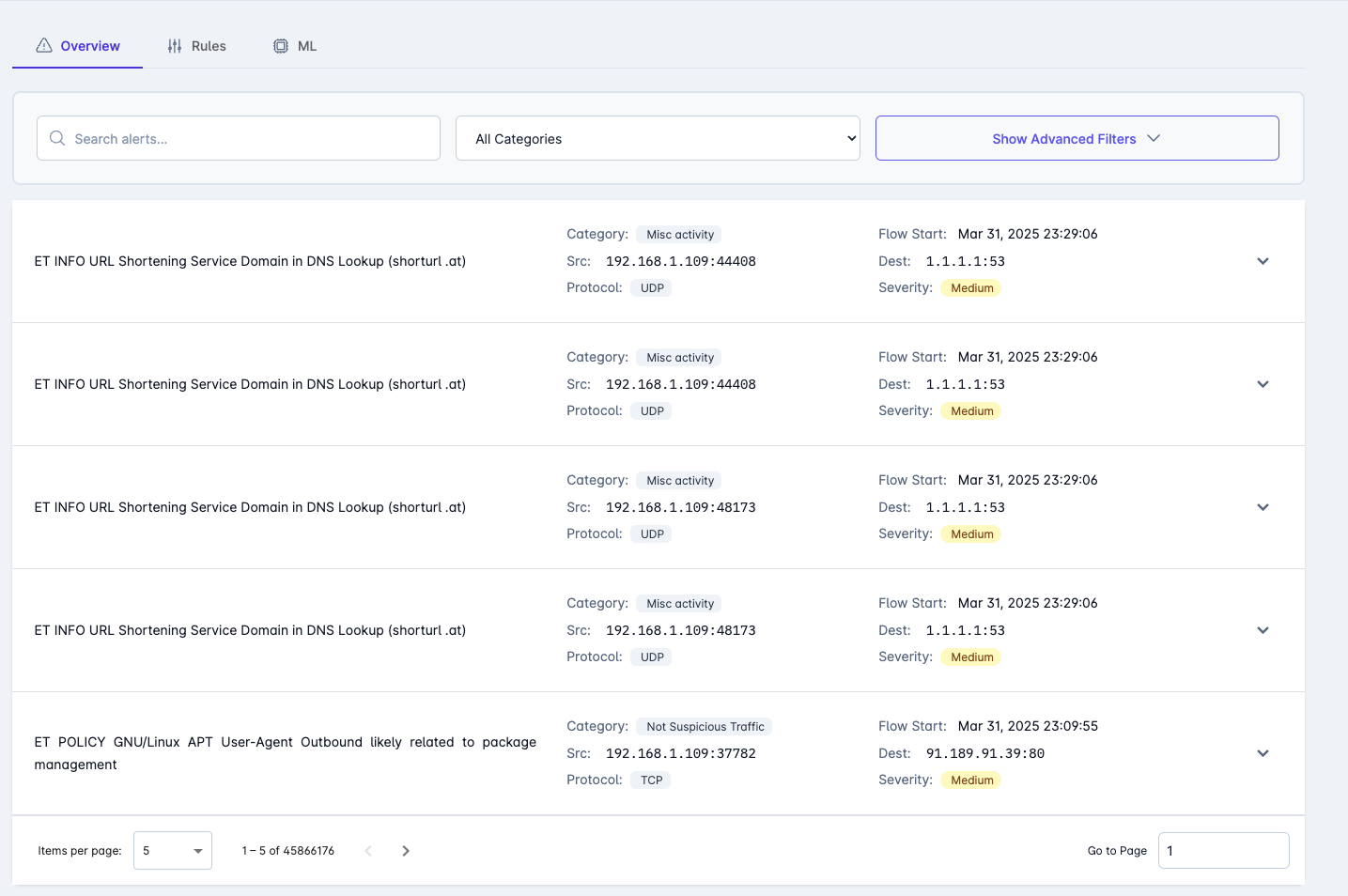
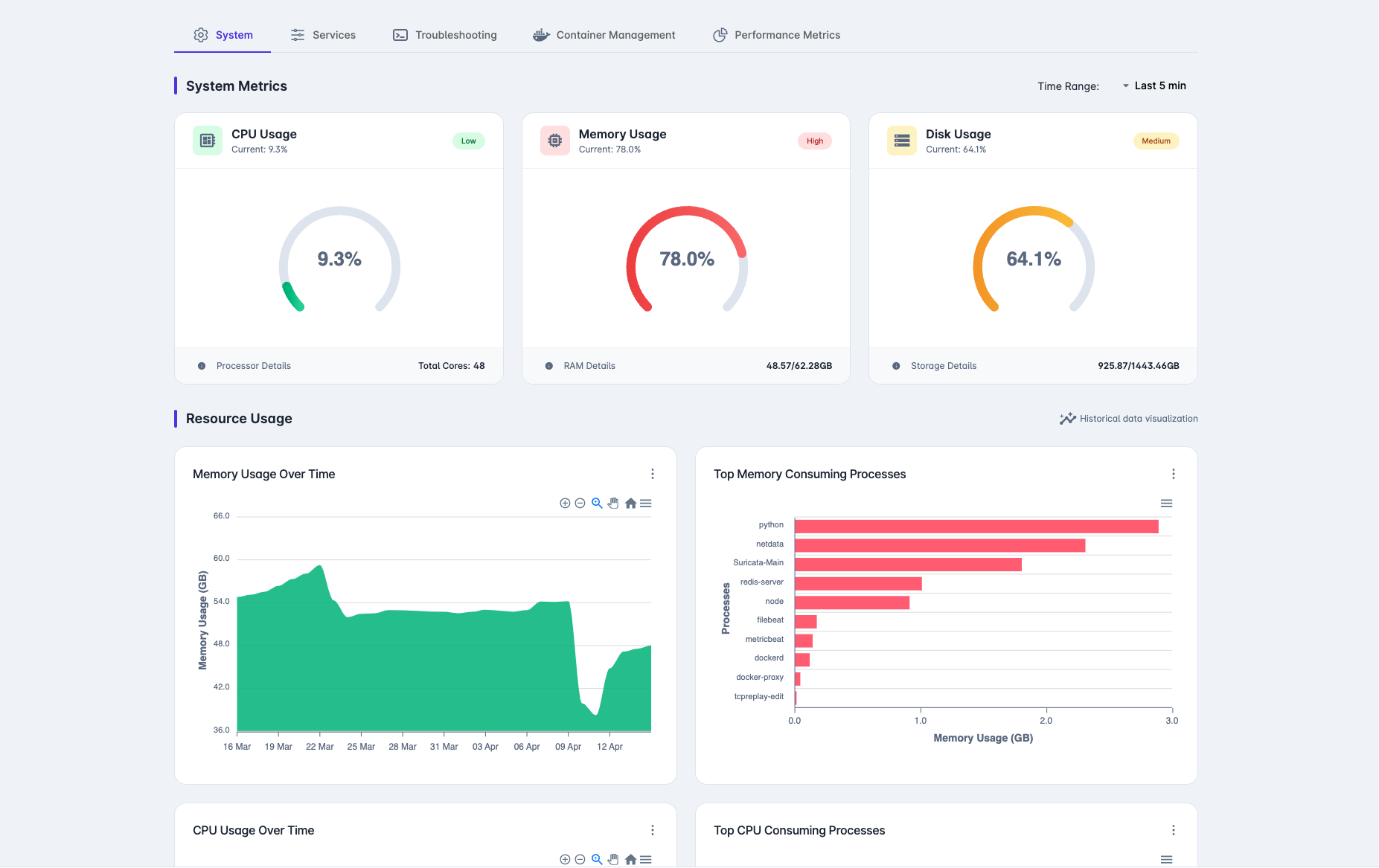
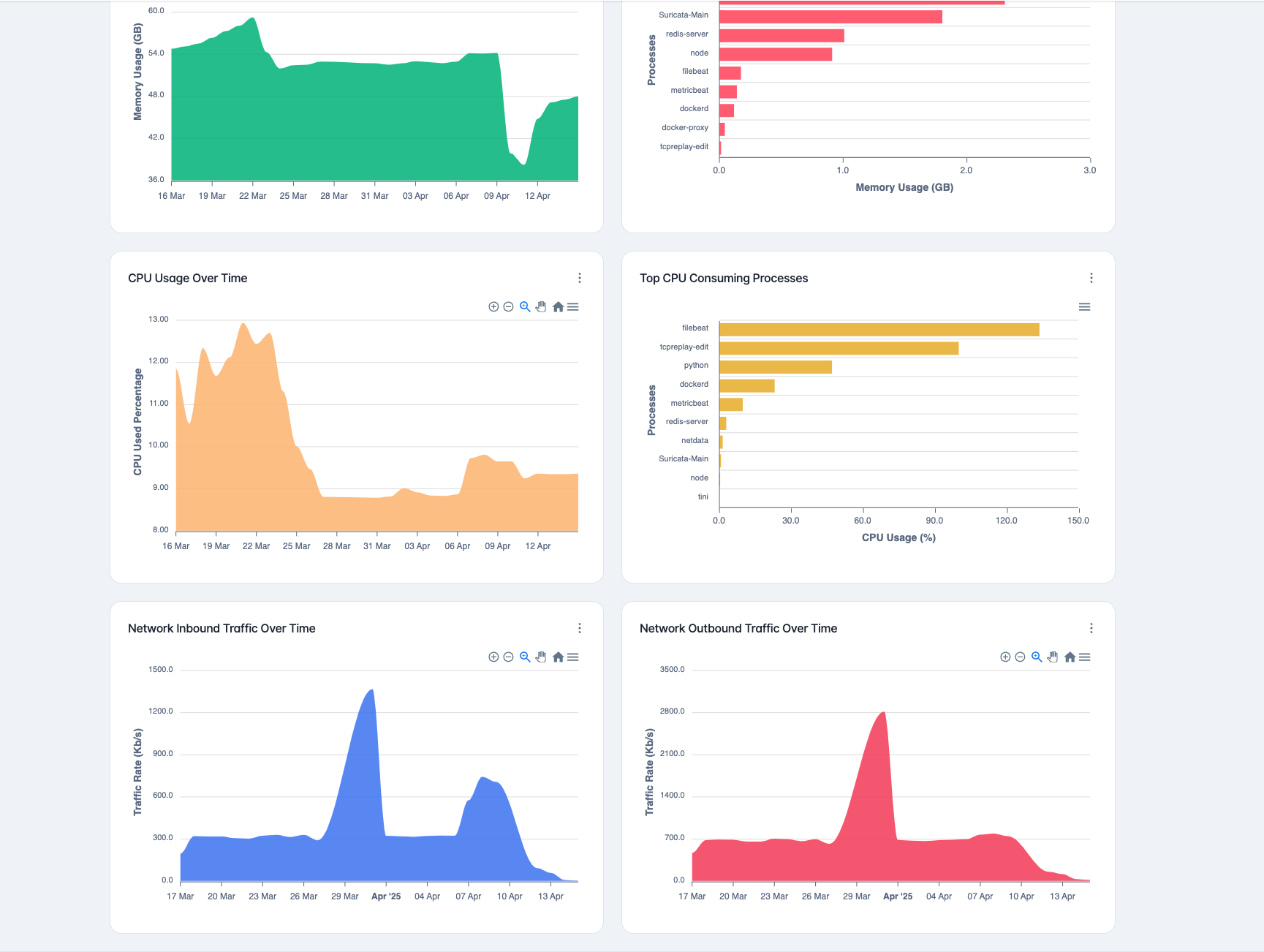
Advanced Network Security
HARES NET combines traditional signature-based detection with cutting-edge AI-driven anomaly detection to provide comprehensive network security. This hybrid approach ensures both known threats and zero-day attacks are identified quickly.
Key Features
Real-Time Traffic Analysis
Continuous monitoring of network traffic with instant alerting for suspicious activities
Behavioral Analytics
Machine learning models that establish behavioral baselines and detect deviations
Sovereign Deployment
Complete control over your security data with on-premises or private cloud deployment options
Integration Capabilities
Seamless connectivity with SIEM platforms, EDR solutions, and other security tools
Technical Specifications
Core Engine
- Suricata IDS/IPS integration
- Customizable rule engine
- Trained anomaly detection models
- Real-time packet processing
Deployment Options
- Docker containerization
- Kubernetes orchestration
- Virtual appliance
- Hardware appliance
Autonomous Threat Hunting Framework
Proactively identify threats before they cause damage
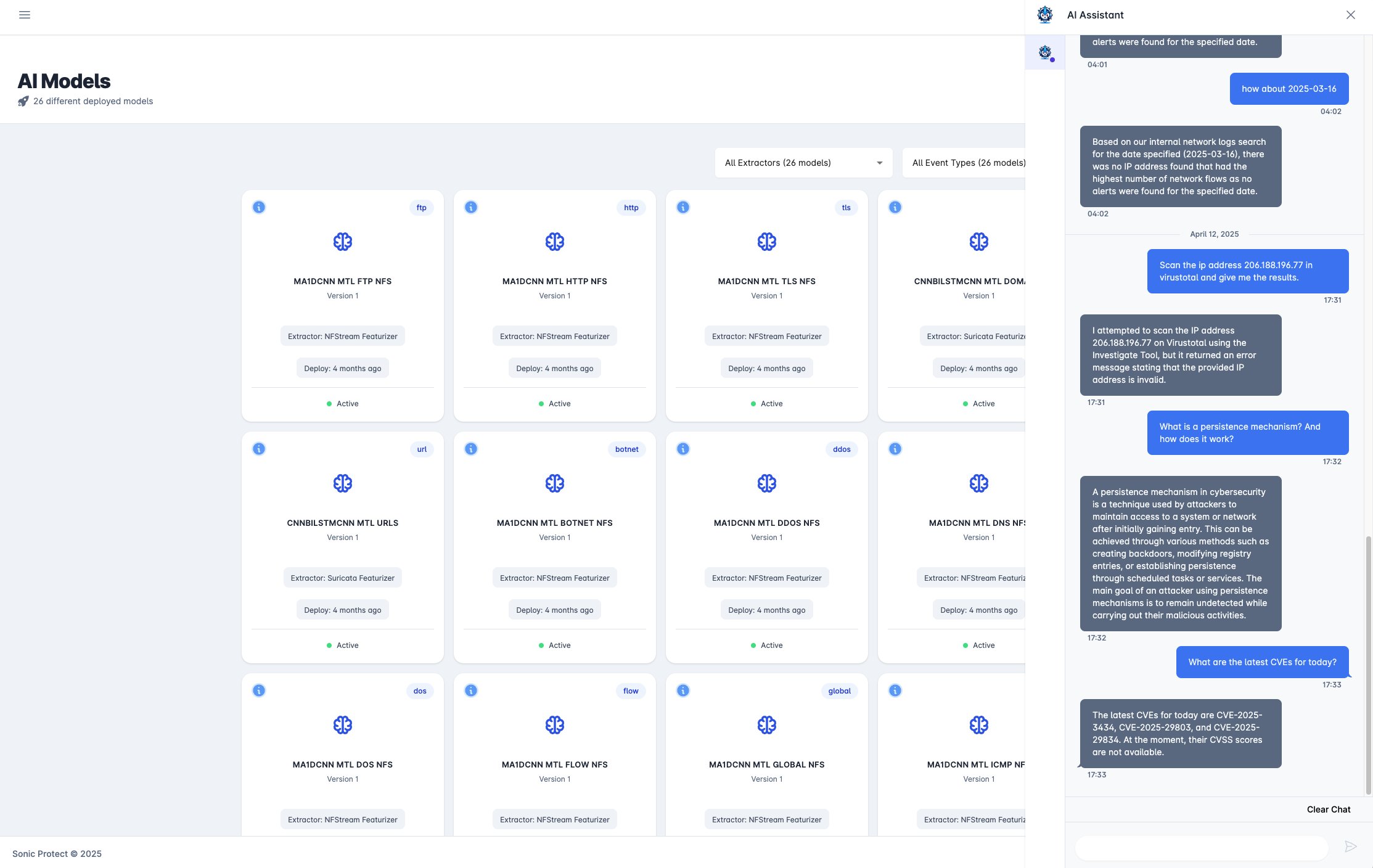

Beyond Reactive Security
HARES Hunter transforms your security posture from reactive to proactive. By using advanced threat intelligence and AI-driven hypothesis generation, Hunter actively searches for indicators of compromise and potential attack paths that traditional security tools might miss.
Key Features
Hypothesis-Driven Investigation
AI generates and tests threat hypotheses based on MITRE ATT&CK framework
Contextual Analysis
Enriches findings with relevant threat intelligence and historical data
Collaborative Hunting
Works alongside human analysts to enhance their capabilities and intuition
Forensic Documentation
Creates comprehensive investigation trails for compliance and knowledge sharing
Use Cases
Adversary Emulation
Hunter emulates known threat actor techniques to test your defenses before real attackers do
Persistent Threat Detection
Identifies long-term, low-and-slow attacks that often evade conventional security tools
Incident Reconstruction
Recreates attack timelines to understand breach mechanics and improve future defenses
Analyst Training
Provides guided hunting experiences that develop junior analysts' skills
AI-Powered Security Operations Center
Virtual Intelligent Bots for Enhanced Response




The Digital SOC Analyst
VIBER SOC represents our vision for the future of security operations: a digital analyst powered by sovereign large language models that works 24/7 alongside your human team, automating routine tasks and enhancing analytical capabilities.
Key Features
Automated Alert Triage
Processes thousands of alerts, prioritizing critical issues that require human attention
Conversational Interface
Natural language interaction allows analysts to query security data using plain language
Cross-Platform Integration
Connects with your existing SIEM, EDR, SOAR and ticketing systems
Automated Reporting
Generates comprehensive incident reports, executive summaries, and compliance documentation
Business Impact
Reduced Alert Fatigue
85% reduction in low-value alerts requiring analyst review
Faster Response Times
60% improvement in mean time to respond (MTTR) to critical incidents
Enhanced Analyst Efficiency
Each analyst can effectively handle 3x more incidents with AI assistance
Knowledge Retention
Preservation of institutional knowledge despite analyst turnover
Why Choose HARES Solutions
Our AI-driven products deliver measurable improvements to your security operations
85% Faster
Reduction in alert triage time with automated processing
300% Increase
In threat detection coverage across network environments
65% Reduction
In mean time to detect (MTTD) critical security threats
90% More
Time for analysts to focus on complex security challenges
Ready to Transform Your Security Operations?
Schedule a demonstration today and see how our AI-powered solutions can revolutionize your SOC workflows.